Log4j Workaround for vRealize Automation 8 and vRealize Orchestrator 8
VMware has been quite busy providing workarounds for all of their products that are affected by the recent Apache Log4j vulnerabilities CVE-2021-44228 and CVE-2021-45046. One of the affected products is vRealize Automation 8.0 through 8.6.1. While VMware has stated that these vulnerabilities will be addressed in the future vRealize Automation 8.6.2 and vRealize Orchestrator 8.6.2 releases, they have provided a temporary workaround as detailed in KB87120 for vRealize Automation and vRealize Orchestrator versions 8.1 through 8.6.1.
I’ll quickly walk through the process of applying this workaround and provide you with an idea of what to expect when applying the workaround. This workaround is persistent over upgrades and the KB should not be re-applied. Additionally, the workaround is meant to be a temporary solution only. Upgrades documented in VMSA-2021-0028 should be applied as soon as they become available.
Applying the Workaround
The first step in the process is to ensure that you have valid snapshots of your vRealize Automation/vRealize Orchestrator appliances before applying the workaround. You should create simultaneous VM snapshots without memory for all nodes in the cluster.
The next step in the process is to connect to one of the vRealize Automation/vRealize Orchestrator nodes via SSH using the root account. It doesn’t matter which node you connect to.
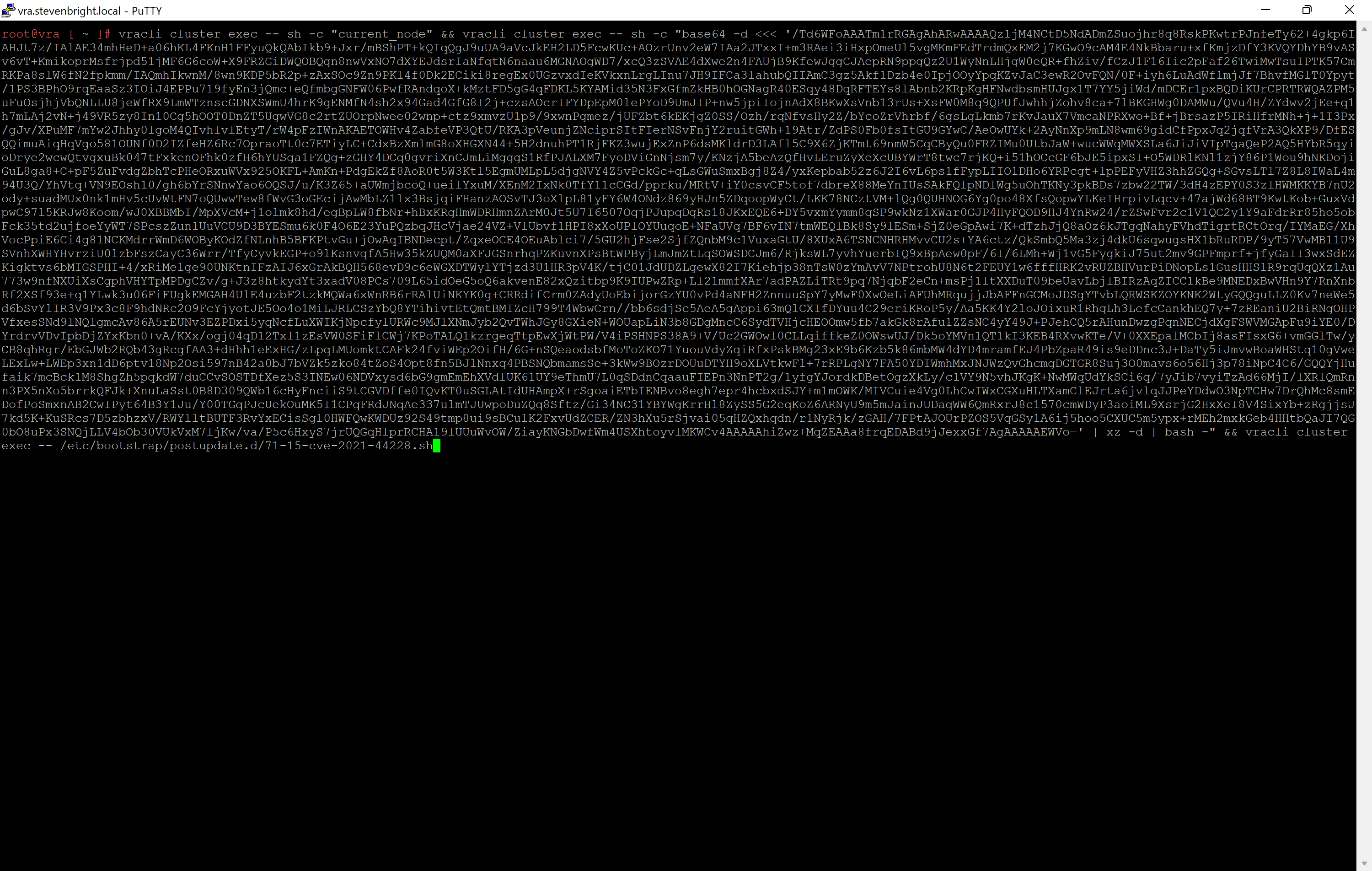
The next step is to execute the command as listed in KB87120. To ensure that you are utilizing the latest workaround, please visit the KB article to obtain this text.
Workaround text being entered into SSH session
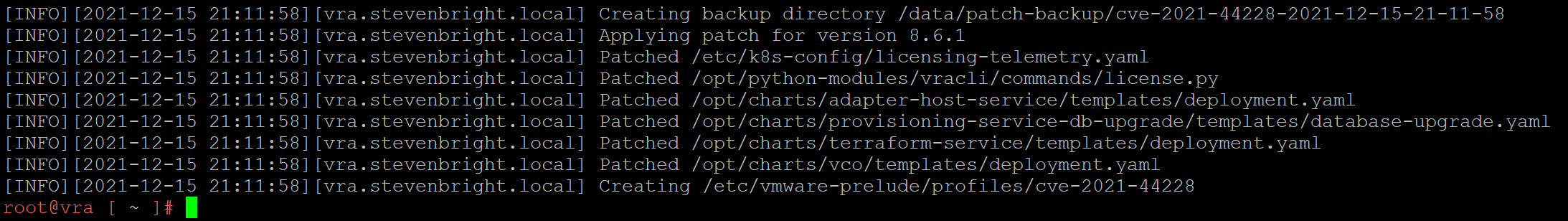
Executing this command will create a backup of all files that will be modified, then it will patch several files. You should see out similar to the below:
The output of the SSH command
The next step in this workaround is to redeploy the vRealize Automation/vRealize Orchestrator Kubernetes pods across all nodes in the cluster. This is accomplished by executing the following command:
/opt/scripts/deploy.sh
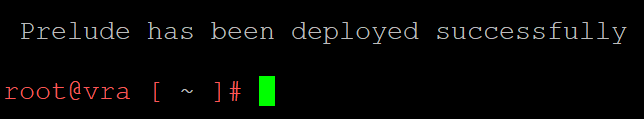
Upon completion of the deployment of the vRealize Automation/vRealize Orchestrator pods, you will see output similar to the below:
Confirmation of successful vRealize Automation pod deployment
Verifying the Workaround
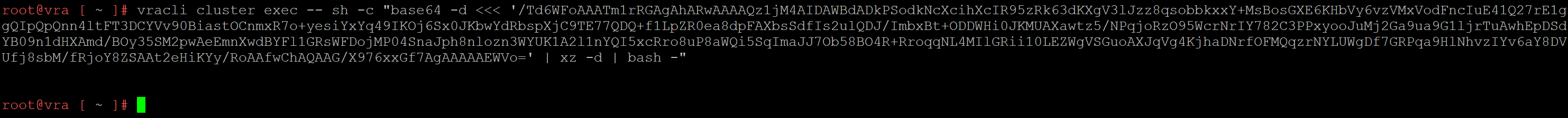
The last step in the process is to verify that the workaround is complete. Again, I will refer you to KB87120 to obtain the proper command so that you will have the latest version of the workaround. If the workaround was successfully applied, you will receive no output from the command as shown:
Expected output to confirm the workaround has been applied
Be sure that you continue to check the current status of VMSA-2021-0028 as updates to address the vulnerability will be listed for all affected VMware products as they become available.
See Also
- VMSA-2021-0028 - VMware's Response to Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) -
- Compliance Management with VMware Aria Automation SaltStack SecOps -
- Introduction to VMware vRealize Automation SaltStack SecOps -
- VMSA-2022-0014: Workspace ONE Access and Identity Manager Critical Vulnerability -
- vRealize Automation 7.6 Cumulative Security Update for April 2022 Now Available -
Search
Get Notified of Future Posts
Recent Posts