Backing Up VMware ESXi TPM Encryption Recovery Keys
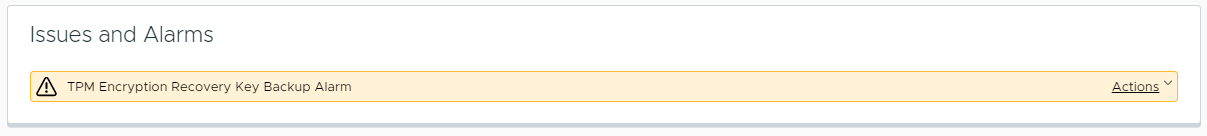
If you have deployed a VMware ESXi 7.0 or 8.0 host containing a TPM 2.0 device, you have likely encountered the “TPM Encryption Recovery Key Backup Alarm” in vCenter reminding you to back up your TPM encryption recovery key.
If you’re like me, the first time you encountered this, you probably searched Google for this alarm message and ran across VMware KB81661 - “TPM Encryption Recovery Key Backup” warning alarm in vCenter Server. You quickly learned that starting with VMware vSphere 7.0 Update 2, any host containing a TPM 2.0 device will now encrypt its configuration files utilizing the TPM 2.0 module. The KB also mentions that it’s possible that a host may not boot if it encounters an issue during the decryption process.
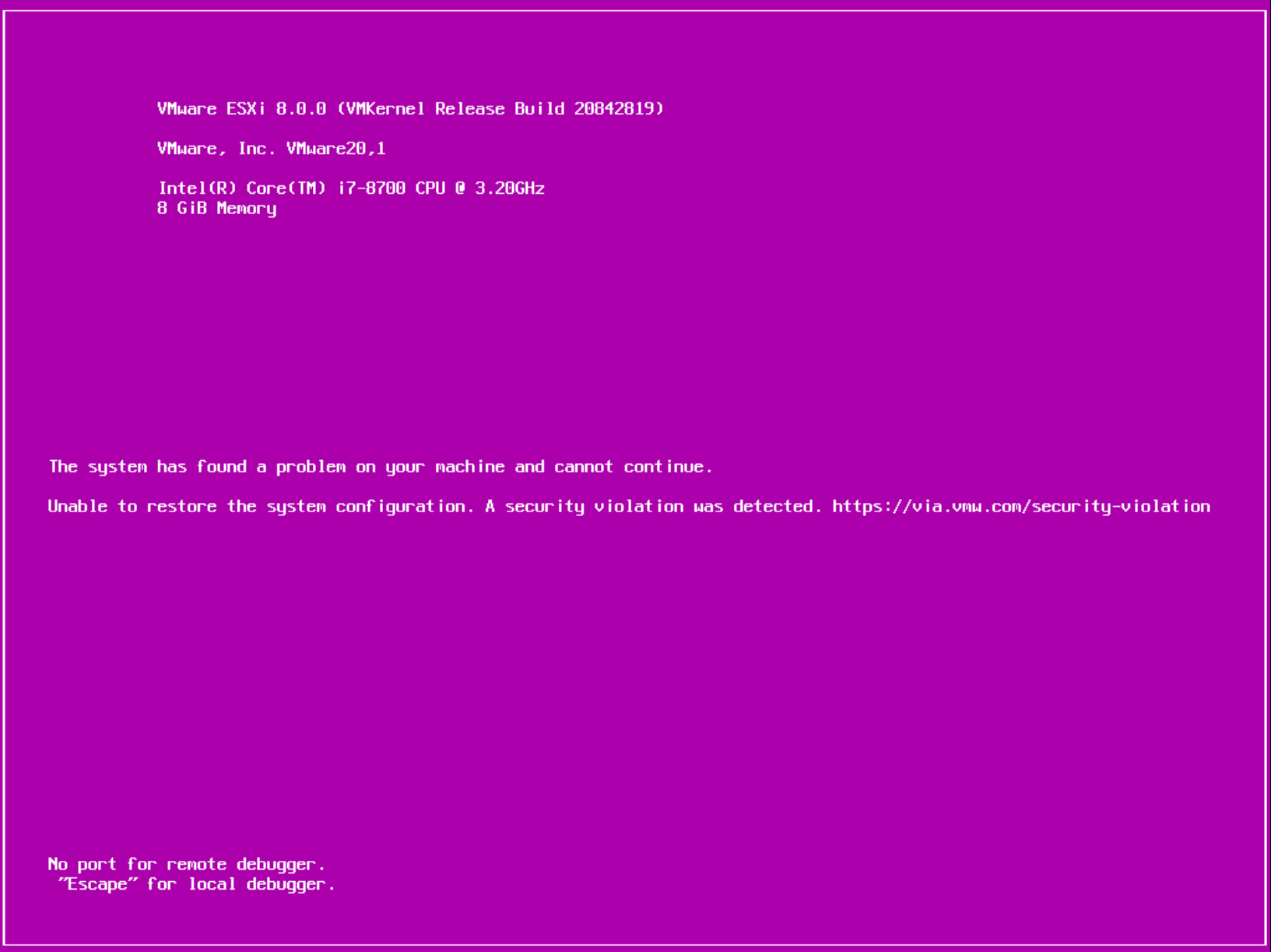
What might cause this type of issue? You might have cleared the TPM (oops!), have a failed TPM device, or replaced the motherboard in your ESXi host. If this occurs, your host will begin the normal boot process and you’ll think everything is working out great until you are presented with a nice purple screen of death (PSOD) that looks like the following:
Not to fret though! You backed up that recovery key, right? If so, you can reboot the host, press Shift + O before the boot begins, provide the recovery key on the command prompt by adding encryptionRecoveryKey=recovery_key, and everything will work out.
If you haven’t backed up that recovery key yet (I didn’t at first), here’s a short PowerCLI script to help you capture all of your TPM Recovery Keys for easy archiving. You’ll need to connect to your VMware vCenter Server utilizing the Connect-VIServer command, then execute the following script:
$VMHosts = Get-VMHost | Sort-Object
$VMHostKeys = @()
foreach ($VMHost in $VMHosts) {
$esxcli = Get-EsxCli -VMHost $VMHost -V2
try {
$encryption = $esxcli.system.settings.encryption.get.Invoke()
if ($encryption.Mode -eq "TPM")
{
$key = $esxcli.system.settings.encryption.recovery.list.Invoke()
$hostKey = [pscustomobject]@{
Host = $VMHost.Name
EncryptionMode = $encryption.Mode
RequireExecutablesOnlyFromInstalledVIBs = $encryption.RequireExecutablesOnlyFromInstalledVIBs
RequireSecureBoot = $encryption.RequireSecureBoot
RecoveryID = $key.RecoveryID
RecoveryKey = $key.Key
}
$VMHostKeys += $hostKey
}
else
{
$hostKey = [pscustomobject]@{
Host = $VMHost.Name
EncryptionMode = $encryption.Mode
RequireExecutablesOnlyFromInstalledVIBs = $encryption.RequireExecutablesOnlyFromInstalledVIBs
RequireSecureBoot = $encryption.RequireSecureBoot
RecoveryID = $null
RecoveryKey = $null
}
$VMHostKeys += $hostKey
}
}
catch {
$VMHost.Name + $_
}
}
$VMHostKeys
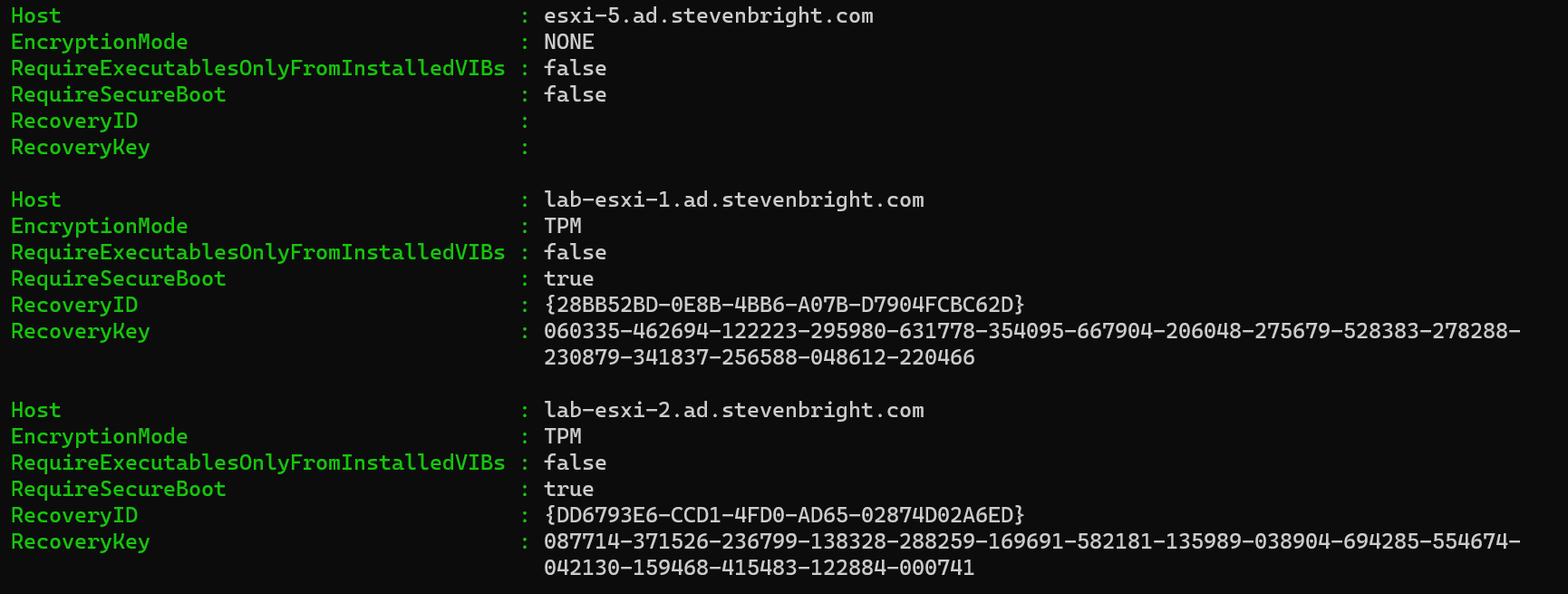
The script interrogates each VMware ESXi host connected within the VMware vCenter Server and lists its current encryption mode, whether or not enforcement of execInstalledOnly is enabled, whether or not UEFI Secure Boot is required, the recovery ID, and the recovery key. The output should be similar to the following:
If you would like to capture this information for backup purposes (as VMware recommends), you can easily add an | Export-Csv filename.csv option to the last line of the script to capture the data in a file. Notice that the first host in the list does not provide any recovery key information. This is because this host does not contain a TPM 2.0 device; thus, its encryption mode is set to NONE.
Now that you have an easy method for capturing all of your recovery keys, be sure to store this information with care and keep it private. If you install any new ESXi hosts or replace any hardware, be sure to run the script again and update your archive.
See Also
- Managing ESXi Local User Accounts from vCenter Server Using PowerCLI -
- Deploy Salt Minions Automatically Using VMware Tools -
- Getting Started with the Synology Storage Console for VMware -
- Automated Snapshot Cleanup with VMware Aria Operations -
- Managing ESXi Local User Accounts from Aria Automation Orchestrator -
Search
Get Notified of Future Posts
Recent Posts